
A System to Detect Sudden Epileptic Attacks Using Radio Frequency Technology | Project Ideas for BME - YouTube

Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News
How to Hack Radio Frequencies: Hijacking FM Radio with a Raspberry Pi & Wire « Null Byte :: WonderHowTo
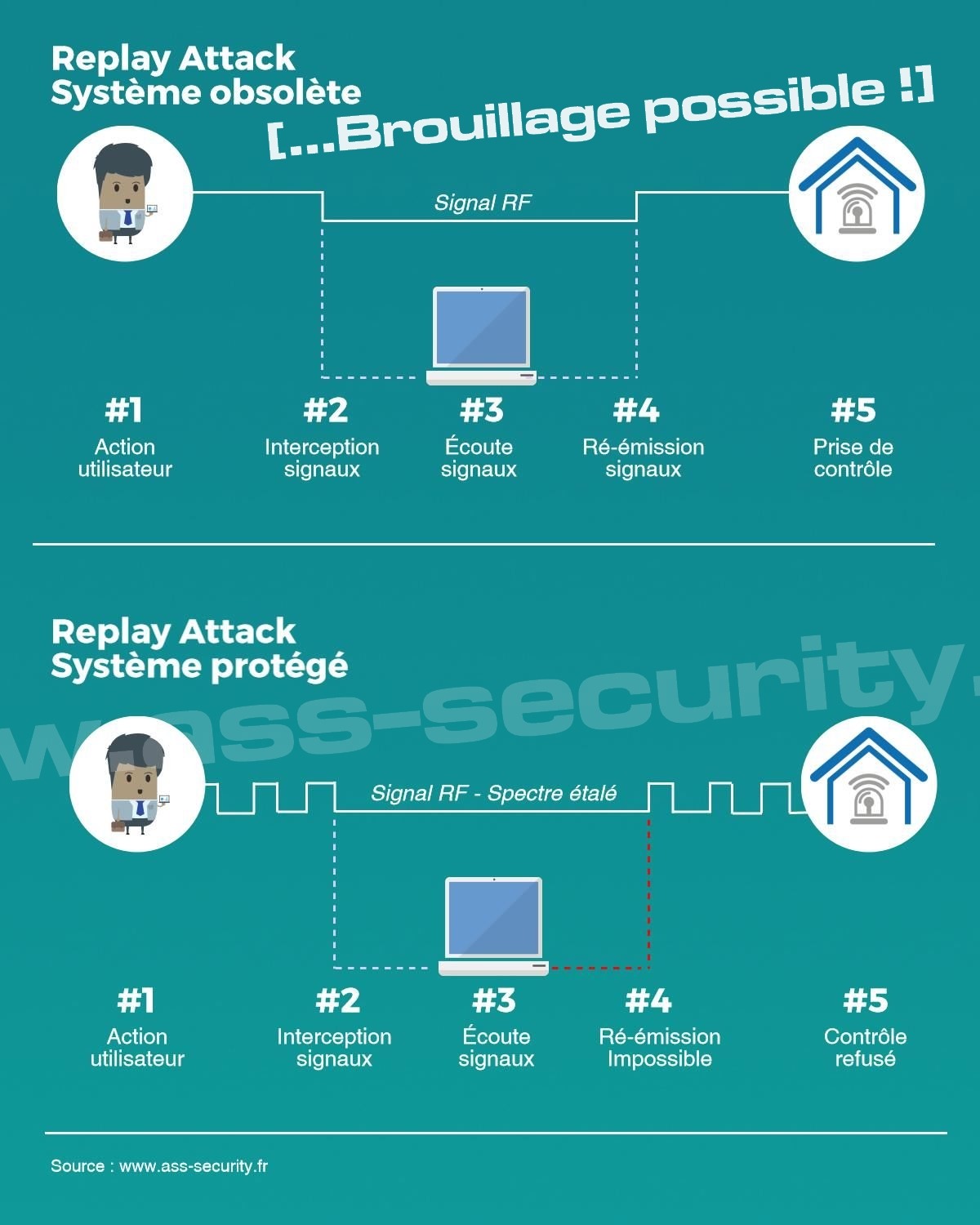
Dossier : Alarme sans-fil, Brouillage, Piratage d'une alarme Radio, Vulnérabilités, Perturbations...
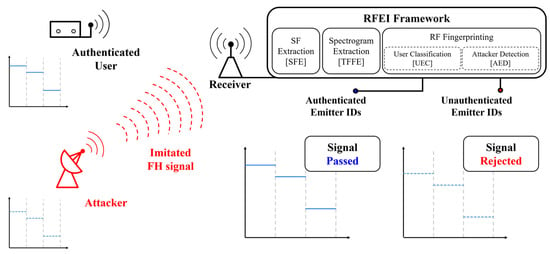
Applied Sciences | Free Full-Text | Radio Frequency Fingerprinting for Frequency Hopping Emitter Identification

Radio Frequency: An Airbone Threat to Corporate and Government Networks | 2020-07-06 | Security Magazine

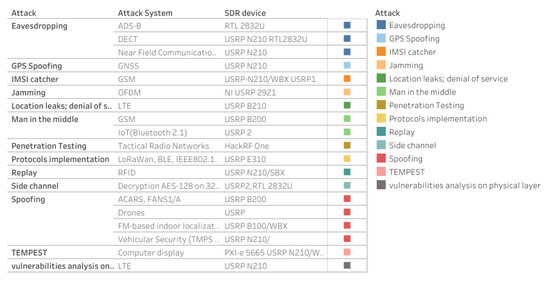

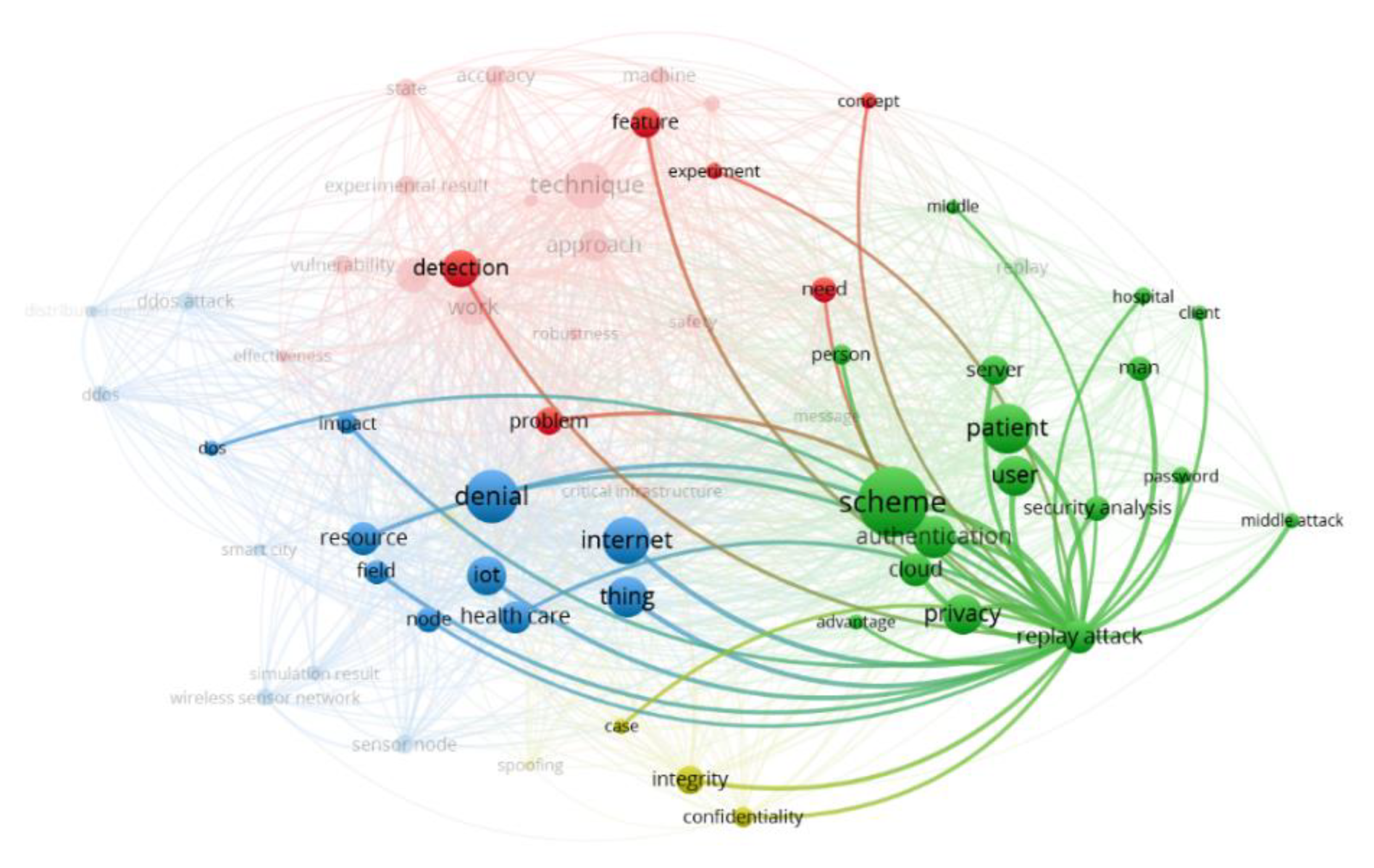
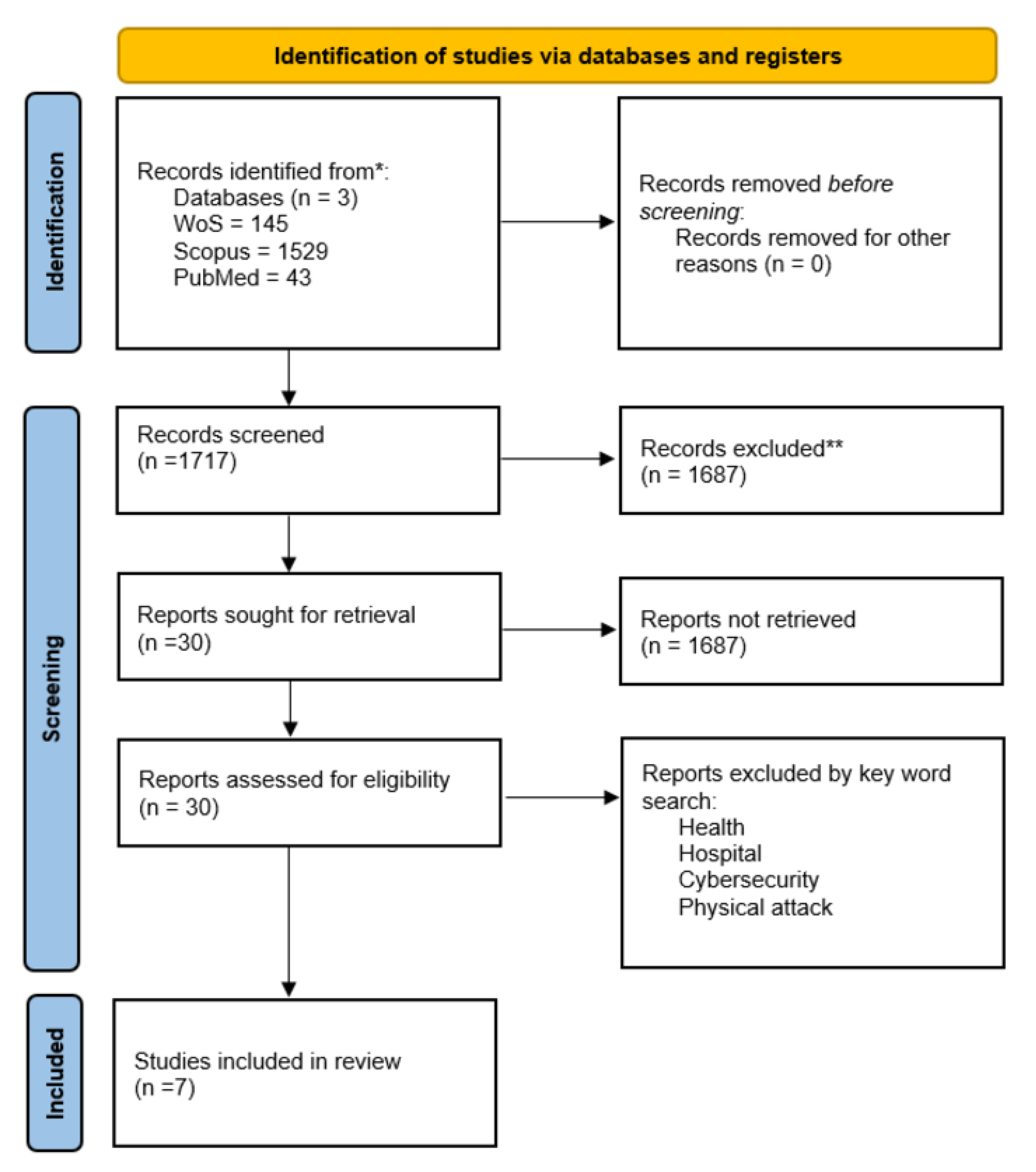

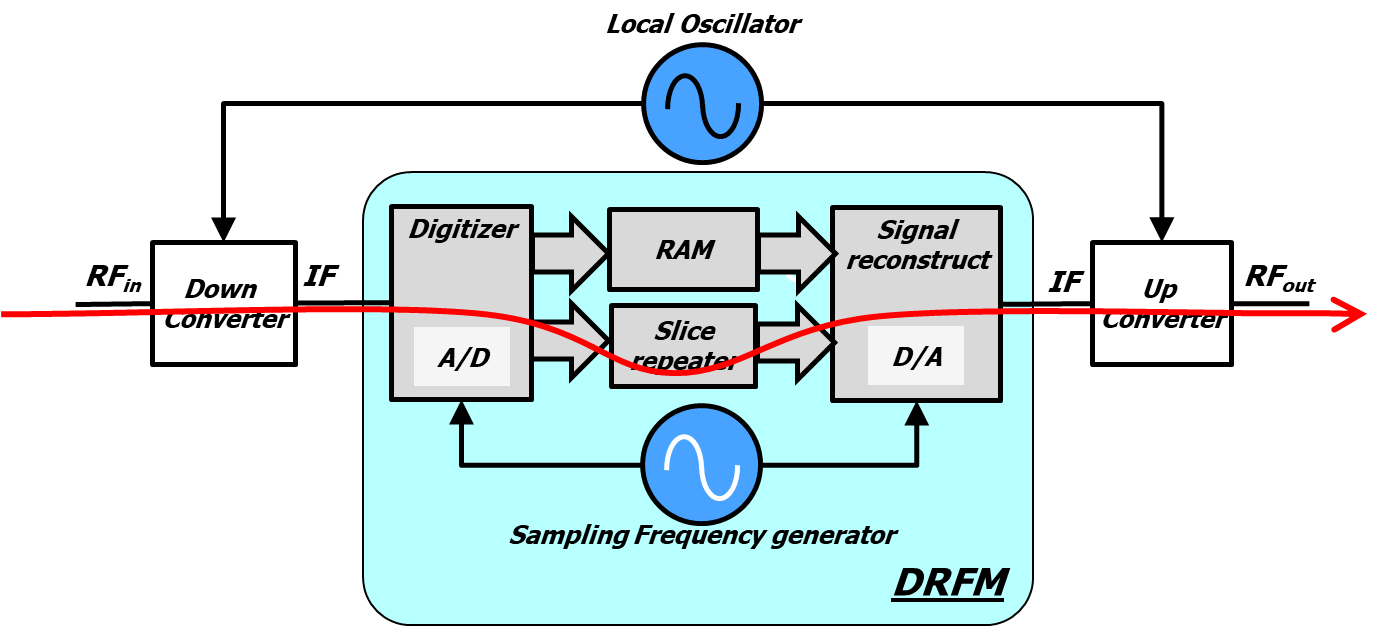


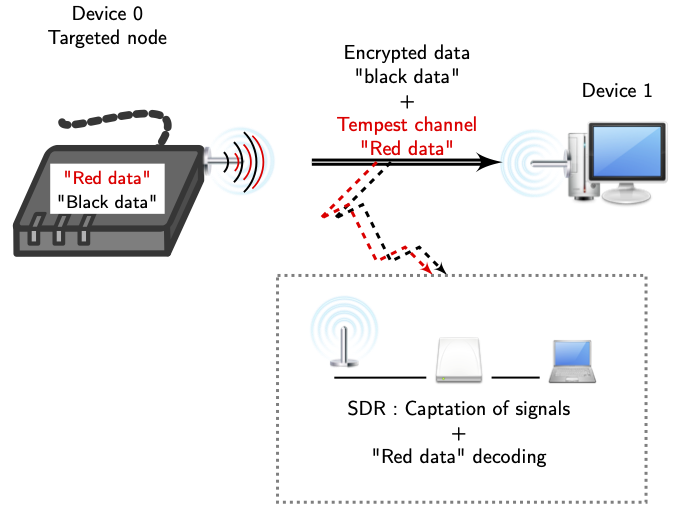

![PDF] A Feasibility Study of Radio-frequency Retroreflector Attack | Semantic Scholar PDF] A Feasibility Study of Radio-frequency Retroreflector Attack | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b64cba7e85681d499801edc80460d0966c79ffcd/2-Figure1-1.png)


